
Tails and IP Addresses
Share
Tails for Anarchists
Tails is a privacy-focused operating system that enables anonymous computing with minimal traces. It’s designed to run from a USB drive or DVD—isolated from the host system—and aims to leave no residual data unless you explicitly choose to preserve something. Bundled with pre-configured security tools, it helps activists, writers, researchers, and others maintain safer communication and operations.
This guide distills the core Tails documentation and adds notes especially relevant to an anarchist threat model. Consider reading our companion Tails Best Practices piece for more advanced strategies.
What Is Tails?
Tails (The Amnesic Incognito Live System) is a Linux-based distribution that offers three main features:
-
Live system
Instead of running from the computer’s internal drive, Tails boots from an external USB, SD card, or DVD. This ensures your internal drive remains untouched. -
Amnesia
The system runs entirely in RAM and does not write to the host machine. On shutdown, all session data is erased. The only data that can persist is what you explicitly save to a designated encrypted partition. -
Incognito / anonymity
All connections are forced through the Tor network. Direct internet connections are blocked by default. Tails also attempts to mask hardware identifiers such as MAC addresses, reducing traceability.
Tails is open source and regularly audited. However, its security depends heavily on correct usage and regular updates. Always verify your installation to avoid tampered versions.
Threat Modeling & Limitations
Tails offers strong protections, but it isn't magic. It doesn't defend against all possible attack vectors, such as:
- hardware or firmware backdoors or compromises
- human error (e.g. revealing identifying information)
- malware or exploits already present in the system
- extremely well-resourced adversaries (e.g. state actors) using sophisticated correlation or timing attacks
Before using Tails for sensitive work, build a threat model: ask who might be targeting you, what they can do, and what damage they'd cause if they succeeded. This helps you tailor your practices more realistically.
Advanced Tips, Tooling & Theory
How Tor Works
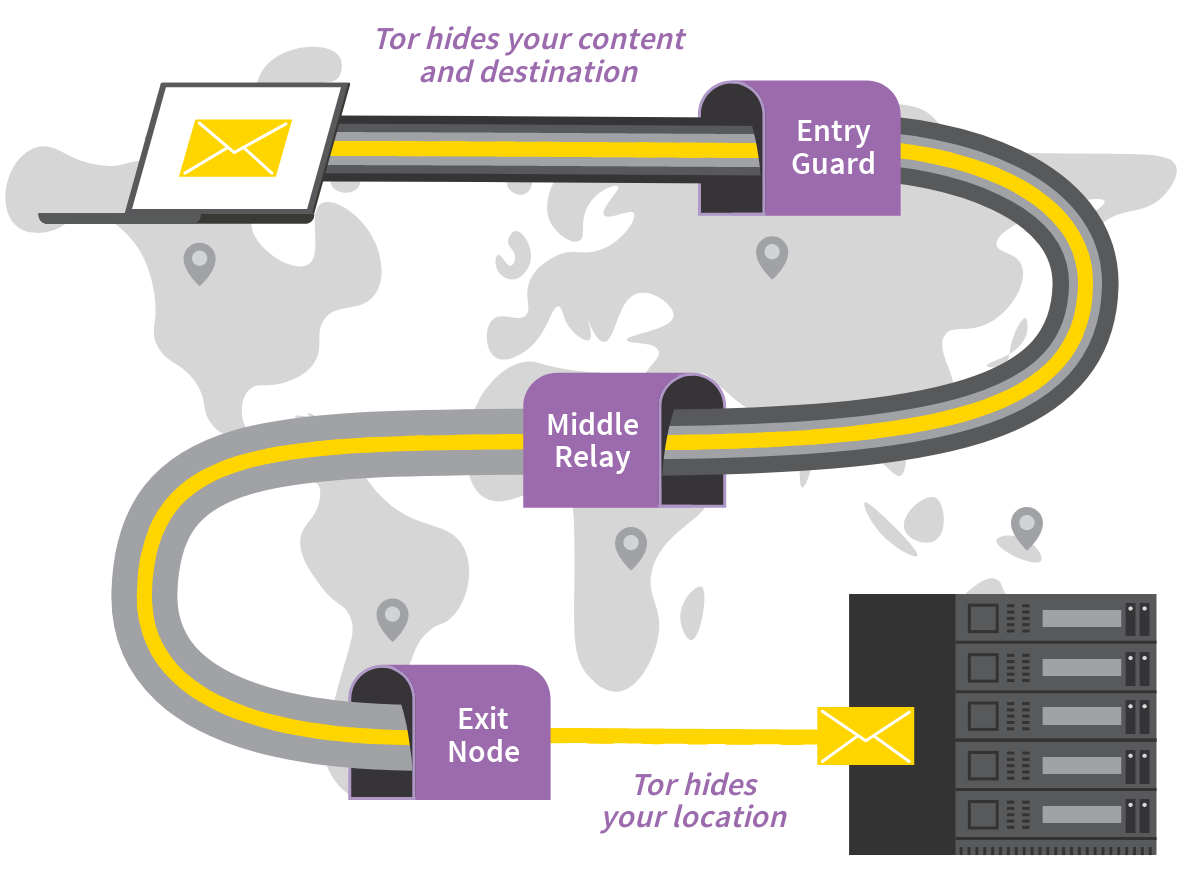
Tor (The Onion Router) anonymizes traffic by routing it through multiple relays. Each relay sees only the hop before and after it—no single node sees the full path.
- The entry relay knows your source IP but not destination.
- The exit node sees the destination but not your origin.
- Using HTTPS is crucial: it encrypts your communications past the exit node, protecting you from detection or manipulation.
- Avoid HTTP-only sites, as intermediaries could eavesdrop or alter data.
Onion Services (".onion")
Websites with .onion addresses are fully enclosed in Tor, meaning both the client and the server remain anonymized. Connections are routed entirely within Tor, without needing an exit node.
These hidden services avoid the usual vulnerabilities of standard websites because the site’s physical location is concealed. If a site offers both a normal domain and an .onion address, prefer the .onion version when possible.
Dealing with Tor-blocking Sites & CAPTCHAs
Some websites block Tor users entirely or require CAPTCHAs or additional verification. If an exit relay is blocked, you can change your Tor circuit (in the Tor Browser, “New Tor circuit for this site”) to try a different path.
If the whole Tor network is blocked, you may need to use a proxy or fallback method—but these are less secure and should be a last resort.
Compartmentalizing Online Identities
Do not mix unrelated identities in the same session. For example, use separate Tails boots when switching between a personal identity and an anonymous one. Restarting Tails is safer than using “New Identity” inside the browser, because browser-based methods don’t reset all underlying Tor circuits.
Tor Browser Security Settings
By default, the Tor Browser is in “Standard” mode. But many exploits are mitigated in more restrictive modes. We strongly recommend switching to Safest before browsing, especially for sensitive work. In this mode, scripts, media, and dynamic content are limited.
You may loosen settings on trusted sites if needed—but always with caution.
File Downloads & Uploads
Because Tails isolates the Tor Browser in a sandbox, downloaded files initially reside inside that sandbox folder. You must move them out manually to work on them. Similarly, to upload a file, first move it into the Tor Browser folder.
Be mindful of your system’s RAM: Tails runs in memory, and large files may exhaust it, causing instability. For large transfers, consider enabling persistent storage or using an external encrypted USB.
OnionShare
To share files without attaching a USB, use OnionShare (bundled in Tails). It creates a temporary .onion link allowing recipients to download the file. Once your session ends, the link is no longer valid.
You can disable the “one-download-only” option if you intend to allow multiple downloads in that session.
Mitigating Traffic Correlation
Adversaries might try to match patterns in network timing or traffic volume ("correlation attacks"). You can make these harder by:
- Disabling JavaScript (using Safest mode)
- Avoiding multiple simultaneous connections
- Limiting identifiable activity in each session
These don’t eliminate the risk entirely, but they increase your anonymity margin.
Useful Built-In Tools
- KeePassXC – a password manager. Use separate vaults for different projects, even if you use the same master password. This limits collateral exposure if one vault is compromised.
- Data wiping – Simply “deleting” files doesn’t remove them securely. On USBs or flash media, you must reformat or overwrite with zeros to reduce recoverability.
- Encrypted USB (LUKS) – For persistent or sensitive data outside Tails, format a USB with LUKS encryption using the “Disks” utility, overwrite existing data, and protect with a strong passphrase.
- File encryption (PGP) – Use Kleopatra (or other PGP tools) to encrypt files before saving them to any USB. Always do decryption inside Tails (in RAM).
- Privilege escalation / administration mode – By default, Tails runs without an administrative (root) password. If you enable one on the Welcome Screen, it’s only valid for that session, letting you run privileged commands or install software. Use this sparingly.
- Installing extra software – You can only add software packages if you enable the feature in Persistent Storage, and then only if each package is safe and properly configured to use Tor.
- Backups – USBs fail or get lost. Back up your data (especially from Persistent Storage) using encrypted drives or off-site solutions.
- Privacy screen – A physical privacy filter on your screen can help prevent shoulder-surfing or covert camera observation.
Troubleshooting & Common Issues
- USB doesn’t boot — Check for compatibility, ensure the BIOS/UEFI is set to boot from USB, or try the “Troubleshooting Mode” in the boot menu. Consult the Tails Known Issues list.
- Tails used to work, now it doesn’t — The upgrade might have failed. Try manual upgrade or reinstallation. Your Persistent Storage, if intact, should still be accessible from a working Tails session.
- Captive portal (Wi-Fi login) — Enable the Unsafe Browser only for that session to access the portal’s login page. Afterwards, revert to the safer mode.
-
USB space issues — Hidden files (like
.Trash-xxxx) may consume space. Turn on “Show hidden files” in your file browser and clean up. -
Files stuck in read-only mode / locked — Locate and delete corresponding
.lockfiles after revealing hidden files, or adjust file permissions. - Cannot install Tails onto USB — The USB may be defective, incompatible, or needs reformatting. Consider using a different USB.
- System performance issues / crashes — Close unnecessary applications or force shutdowns if needed. Adding more RAM may help.
- Printer setup — Go to Settings → Devices → Printers, then add a printer. Some models may not work reliably.
-
Software installation problems — If the Synaptic Package Manager fails, open a root terminal and run
apt update && apt install <package>.
Best Practices & Final Thoughts
Using Tails effectively means combining technical tools with cautious habits. Before undertaking any high-risk activities—publishing anonymous content, coordinating protest logistics, or handling sensitive leaks—ensure you’ve internalized these practices:
- Always verify your Tails download.isabling JavaScript (using Safest mode)
- Keep Tails up-to-date.
- Segment identities and avoid mixing them in a single session.
- Prefer .onion services and HTTPS.
- Limit use of Persistent Storage and never store overly sensitive data on the Tails USB itself.
- Use external, encrypted USBs for permanent storage.
- For file sharing, OnionShare is safer than passing USB sticks.
- Watch out for correlation or fingerprinting attacks.
- Be cautious when installing extra software and only do so when you trust it.
Tails makes powerful tools accessible, but the ultimate security depends on you: how well you understand your threat model, how disciplined you are, and how rigorously you follow the principles of compartmentalization and minimal exposure.
If you like, I can also generate a version tailored to your specific threat model (e.g. activist in a high-surveillance country) or a shorter “cheat sheet” you can carry with you. Do you want me to do that?

